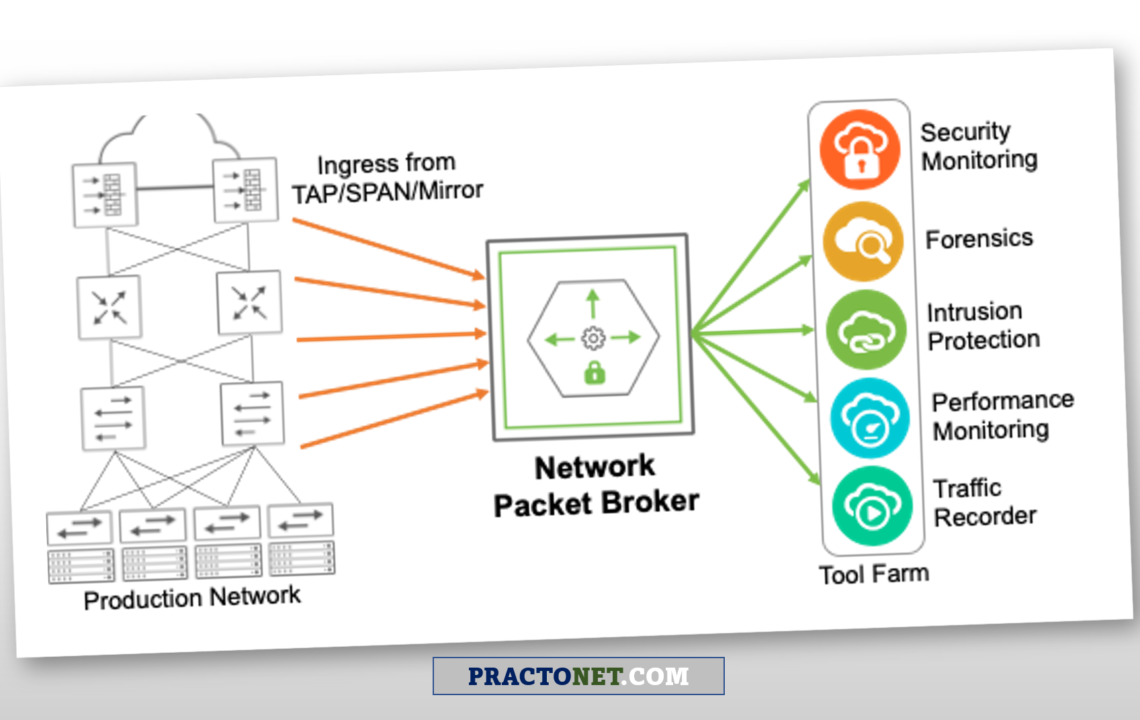
A Network Packet Broker (NPB) resides between taps and SPAN ports. They can access network data and sophisticated security and monitoring tools that typically reside in data centers. NPB’s do just what their name says: they broker network packet data to ensure every
analysis tool sees exactly the data it needs to perform at the highest possible level. The NPB adds an increasingly critical layer of intelligence—one that reduces cost and complexity to help you achieve the following:
Better data for better decisions
A fabric of packet brokers with advanced filtering capabilities serves to organize and streamlinedata for your monitoring, performance, and security tools.
Tighter security
It is hard to stop threats when you do not see them coming. NPBs work to assure that your firewalls, IPSs, and other defenses see exactly the right data, all of the time.
Faster problem resolution
Zeus Kerravala, principal analyst at ZK Research, observes, “Problem identification is IT’s biggest challenge.” Identifying that there is, in fact, an issue consumes up to 85% of mean time to repair (MTTR). Downtime is money. Context-aware filtering provided by NPBs helps you detect and determine the root cause of issues faster by introducing advanced application intelligence. Ixia’s robust Security Fabric leverages this intelligence to speed up troubleshooting by providing insight into the geographic location of outages and the vendors that may be causing disruptions.
Increased proactivity
The use of metadata, provided through NetFlow by intelligent NPBs, also aids in accessing the empirical data used to manage bandwidth usage, trending, and growth. That prevents problems from occurring in the first place.
Better return on investment (ROI)
Intelligent NPBs do not merely aggregate traffic from monitoring points the way a switch might. They filter and groom data to enhance the utilization and productivity of security and monitoring tools. With only relevant traffic to process, they help improve tool performance, reduce
congestion, minimize false positives, and achieve better coverage using fewer devices.
What Exactly Does the NPB Do?
Conceptually, aggregating, filtering, and delivering data sounds simple. In practice, intelligent NPBs perform sophisticated functions to produce exponentially higher efficiency and security gains. One way they do this is by load balancing traffic. For example, if you upgrade your data
center network from 1Gbps to 10Gbps, 40Gbps, or higher, NPBs can downshift speeds. That allows you to distribute higher speed traffic across a pool of existing lower-speed 1G or 2G monitoring tools for analysis. This extends the value of your existing monitoring investments and avoids costly rip-and-replace upgrades as you migrate.
Other powerful features and functions the NPB performs include the following:
Deduplicating redundant packets
Analysis and security tools stand to receive a slew of duplicate packets as multiple taps forward traffic. NPBs can eliminate duplicates to keep tools from wasting processing capacity by handling redundant data.
SSL decryption
Secure Socket Layer (SSL) encryption is the standard technology used to safely send private information. However, hackers can hide cyberthreats in encrypted packets. Decryption is necessary to inspect this data, but unraveling code takes valuable processing power. Leading packet brokers can offload decryption from security tools to ensure total visibility while easing the burden on high-cost resource.
Data masking
SSL decryption leaves data visible to anyone with access to security and monitoring tools. NPBs can mask personally identifiable information such as credit card and Social Security numbers, protected health information, and other sensitive data, before passing it on. That means tools and their administrators cannot see it.
Protocol header stripping
An NPB may strip out protocol headers such as VLAN, VXLAN, and L3VPN, allowing tools that process these protocols to receive and process packet data. Context-aware visibility helps in spotting rogue applications running on your network and footprints attackers leave as they work their way through your systems and networks.
Application and threat intelligence
Early detection of breaches mitigates the loss of sensitive information and the ultimate cost. Context-aware visibility that NPBs deliver can expose indicators of compromise, identify the geolocation of attack vectors, and combat encrypted threats.
Application intelligence extends beyond Layers 2 through 4 (of the OSI model) to Layer 7 (the application layer) of the packet data. Creating and exporting rich data about the behavior and location of users and applications helps thwart application-layer attacks featuring malicious code masquerading as normal data and valid client requests.
Application monitoring
Application-aware visibility also has profound implications for performance and management. Maybe you would like to know when employees are using cloud-based services such as Dropbox, or web-based email to bypass security policies and transfer company files. Perhaps former employees are attempting to access files using personal cloud-based storage service.