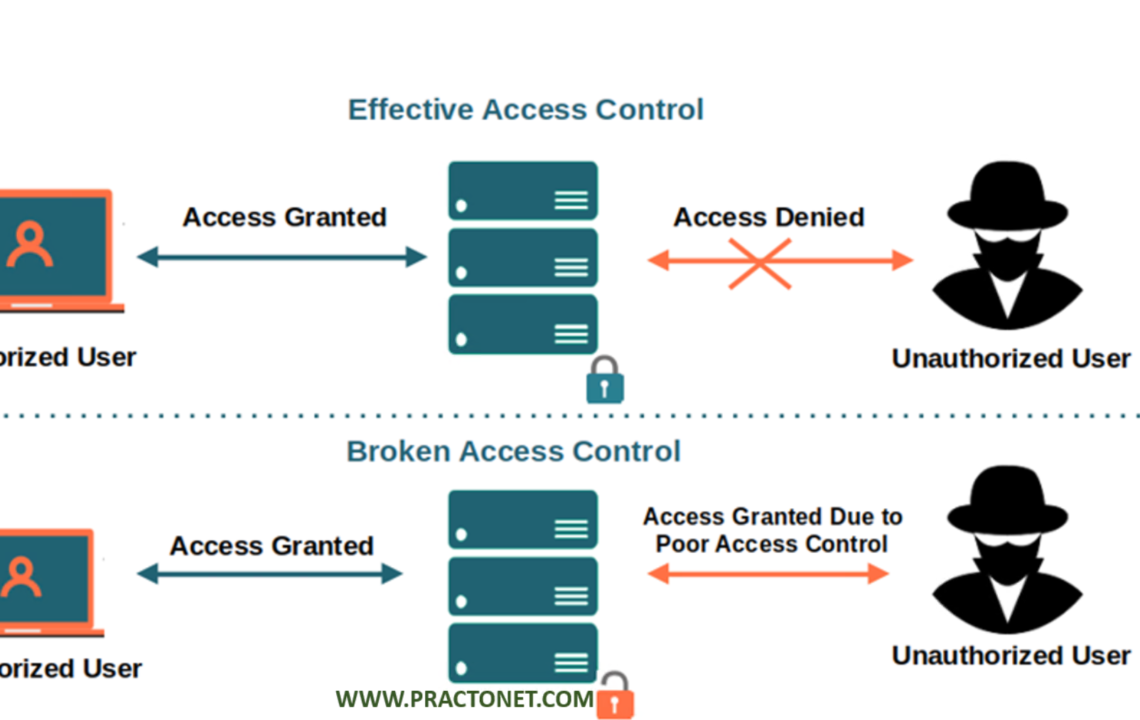
Access control is a crucial element in maintaining the integrity and confidentiality of information. Access control ensures that only authorized users can access sensitive information, thereby protecting it from unauthorized access, modification, or theft. However, if access control measures are not implemented properly, it can lead to a vulnerability called “Broken Access Control,” which can have severe consequences for an organization.
What is Broken Access Control?
Broken Access Control is a vulnerability that arises when an application’s access controls are not implemented correctly, allowing unauthorized users to access sensitive data or perform actions that they should not have access to. This vulnerability can be exploited by attackers to steal or modify sensitive data, take control of the application, or even launch attacks on other systems.
Broken Access Control can occur due to various reasons, including misconfigured permissions, insufficient user authentication, or weak session management. For instance, an application may allow a user to perform a critical action without properly authenticating the user’s identity, or it may fail to check whether the user has the necessary permissions to access a particular resource.
Examples of Broken Access Control: There are several examples of how Broken Access Control can manifest in different scenarios. Let’s look at a few examples:
- Vertical Privilege Escalation: An attacker may attempt to elevate their privileges within an application to gain access to resources they should not have access to. For example, an attacker may try to gain access to an administrator’s account by exploiting a vulnerability in the application’s session management.
- Horizontal Privilege Escalation: In this scenario, an attacker may attempt to gain access to other users’ accounts with the same level of access. For instance, an attacker may try to gain access to another user’s account on a social media platform by exploiting a vulnerability in the application’s session management.
- Accessing Sensitive Data: An attacker may try to access sensitive data, such as financial records or customer data, by exploiting a vulnerability in the application’s access controls. For instance, an attacker may try to bypass authentication and gain access to a company’s financial records.
Consequences of Broken Access Control The consequences of Broken Access Control can be severe, leading to data breaches, financial loss, reputational damage, and legal consequences. If an attacker gains access to sensitive data, they can steal it or modify it, leading to financial losses or identity theft. Additionally, a data breach can harm a company’s reputation, leading to a loss of customer trust, which can have a long-lasting impact on the business.
Preventing Broken Access Control: To prevent Broken Access Control vulnerabilities, organizations should implement the following best practices:
- Implement strong authentication and authorization mechanisms that verify users’ identities and grant them appropriate access levels.
- Implement proper session management, including timeouts, to ensure that users are logged out of the system after a period of inactivity.
- Regularly audit user permissions and access to ensure that users only have access to the resources they require to perform their job duties.
- Conduct regular security testing to identify vulnerabilities in the application’s access control mechanisms.
Broken Access Control is a significant vulnerability that can lead to severe consequences for an organization. To prevent this vulnerability, organizations must implement robust access control mechanisms and regularly test them to ensure they are working as intended. By doing so, organizations can reduce the risk of data breaches, financial losses, and reputational damage.