Proxychains is open source software for Linux systems and comes pre-installed with Kali Linux, the tool redirects TCP connections through proxies like TOR, SOCKS4, SOCKS5, and HTTP (S) and it allows us to chain proxy servers. With proxychains, we can hide the IP address of the source traffic and evade IDS and firewalls.
To setup proxychains you will first need the tor service, most of the time the service is preinstalled. To check if there is tor service available or not just use this command.
First Switch to ROOT user.
sudo -i
Type your password and enter, Now you’re in Root user. so type,
root@kali:~# service tor statusIf you get this output that means TOR is not installed in your system and not running,
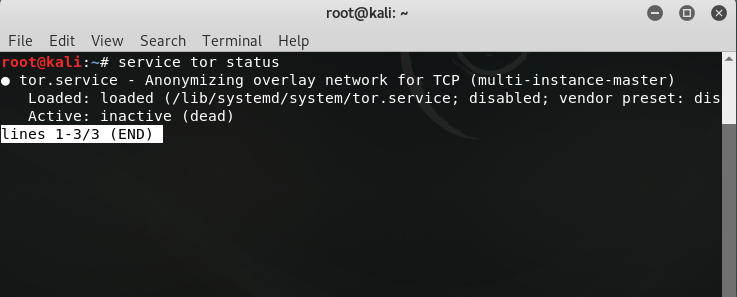
If you get this output that means TOR is installed in your system and running,\
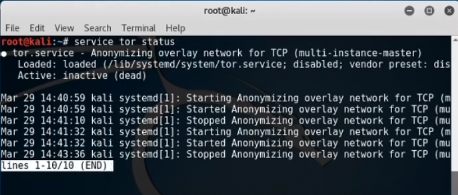
For installing TOR,
root@kali:~# apt-get install tor
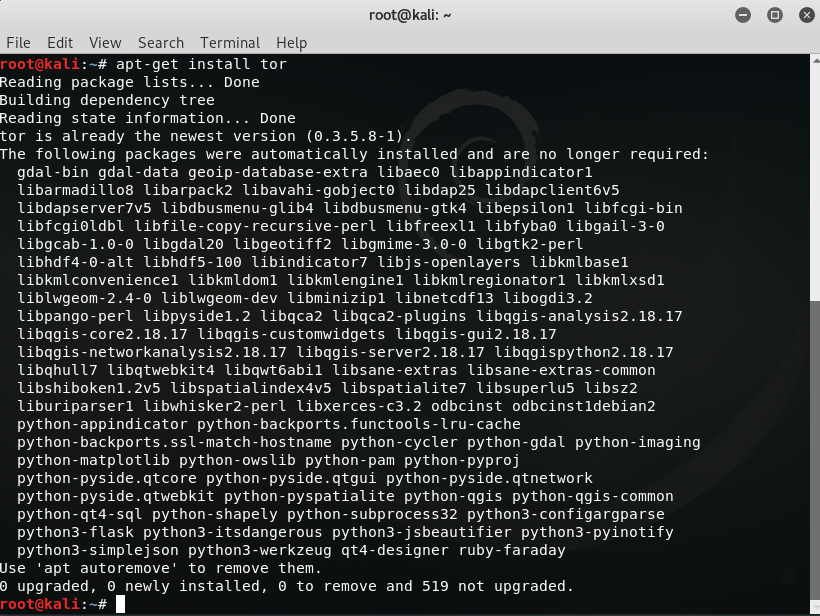
If TOR Successfully installs then, Start TOR service. root@kali:~# service tor start
Now to check the TOR service status. root@kali:~# service tor status
Configure Proxychains
After installing tor service now we need to configure proxy-chains. To do so use the following command.
root@kali:~# nano /etc/proxychains.conf
You see this type of file in the terminal. you will see “#” which means bash language comments. if there is no “#” hash that means it defaults running. or if we remove “#” hash that means we want to run this. You can use arrow keys to scroll down & up and read file content and do the following changes as you need.
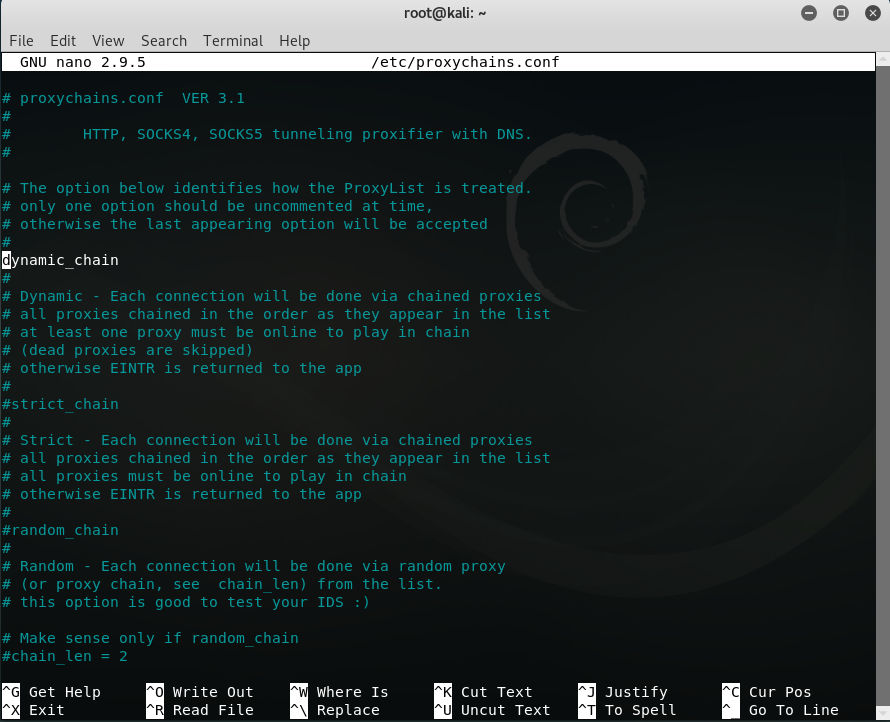
As you see in this there are three types of proxy-chains: 1)dynamic 2)strict 3)random
we’re going to use dynamic chain,
- Remove Dynamic chain from comment
- comment Strict chain and Random chain
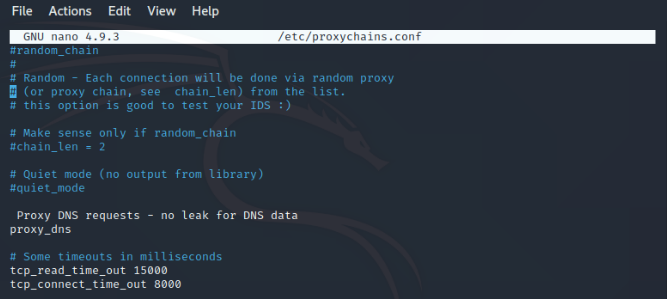
- Remove proxy DNS from comment
- Also, Remove Proxy DNS requests — no leak for DNS data from comment
- Now, write socks5 127.0.0.1 9050 in the last line of the proxy list.

Now just write save by ctrl+o and enter and for exit the file ctrl+X, now exit the terminal.The proxychains setup is completed.
Tips: Here, SOCKS is an internet protocol that routes packets between a server and a client using a proxy server. and socks4 and socks5 is the type of socks.
127.0. 0.1 is the loopback Internet protocol (IP) address also referred to as the localhost.
9050 is port number and By default, Tor listens on this port for socks proxy.
Now Restart your machine,
To start proxychains first restart the tor service and then launch proxychains in firefox with a link for a particular search engine like bing, duckduckgo. Use the following commands:
root@kali:~# service tor restart
Now,
root@kali:~# proxychains firefox www.bing.com
After running the following commands firefox will launch and www.bing.com will load. When you run the command you must not get any error and bing should get loaded. Also please close all firefox tabs before executing the commands.
You can see that after executing the proxychains bing loaded with some other language. Now let’s do a DNS leak test by searching DNS leak test and open any website providing the same.
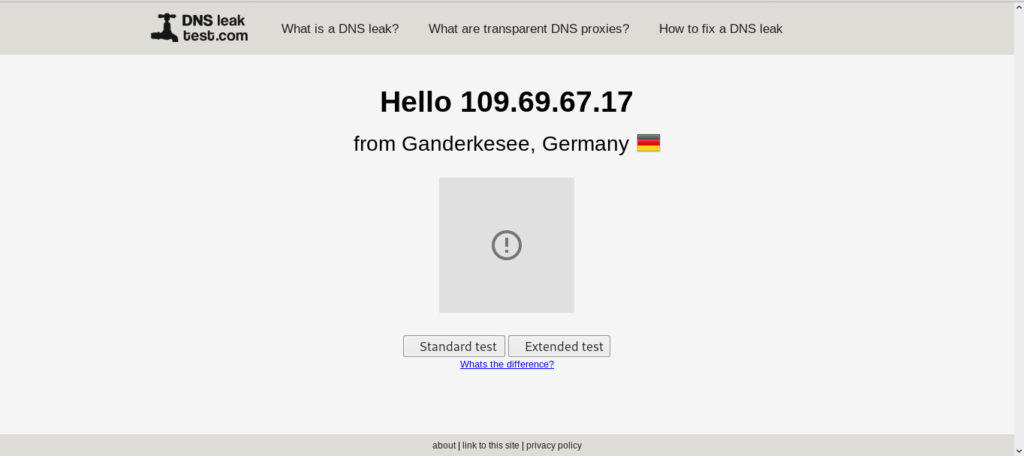
You can see that my location is now changed to GERMANY and the good thing is that proxychains keep on changing my IP address in a dynamic way without leaking my DNS. so that it provides good anonymity. If you want that you see a different result then you can just close the firefox and clear the terminal, restart tor service and again launch proxychains you will see some different results in DNS leak test.





