Cyber criminals will aim to hide their IP public address – the one that can identify them on Internet – while they won’t care too much about the local address, since they will have already wiped their MAC Address, so any data within the local network will not betray them. As you already know, the local IP
address is assigned by a router and is not enough to identify the computer owner, unlike the MAC Address.
It’s worth mentioning that experienced cyber criminals will mostly never work from their home or a nearby network: despite all precautions put in place, they perfectly know they must hide every single trace or evidence, including the “borrowed” network connection used for their attacks. Therefore, they will rely
to one of the oldest IT tools: Proxies. Proxies (technically, open proxies) are servers – called proxy servers – which can perform different operations:
- Provide anonymous navigation
- Copy web pages
- Copy web pages
We must consider that, nowadays, proxies are less and less used for anonymous navigation, since they have been replaced by more effective methods; however, they are still useful in certain scenarios – mainly in programming – therefore you have to know them Basically, proxies lay between a client and a server, acting as in intermediary between them.
Proxy Types
There are many types of proxies, according to different purposes and design specifications. Although it would be useful to understand how they can be smartly used in server infrastructures, here we will only explain the differences in the scope of anonymous navigation.
- Proxy HTTP/HTTPS : As we can tell, HTTP/HTTPS proxies can filter information within the HTTP protocol and its secure form, HTTPS. let’s say that HTTP is a communication protocol designed to parse information at the World Wide Web level. It’s the most popular protocol and has two forms: HTTP (not encrypted), HTTPS (SSL/TLS encrypted). When it comes to HTTP proxies, they are the most popular and easy to find, since servers only have to manage such protocol, and then optimize their machines for that single task. Compared to SOCKS, they are usually more responsive but, naturally, restricted to their protocol. In turn, such types of proxies are broken down into sub-categories according to their “quality”. Although each agency distributing proxies use their own evaluation criteria, we conventionally distinguish 3 levels: Non anonymous proxies, Anonymous proxies and Elite proxies.
- SOCKS4 Proxies : Using a proxy supporting the SOCKS4 protocol instead of HTTP/HTTPS,
- you can reroute any TCP-based data, and it is a huge benefit. This essentially means that you can filter the World Wide Web services – naturally based on TCP as well –but also the whole range of protocols supporting this kind of service. You can also find a variant named SOCKS4a.
- SOCKS5 Proxies : Quite identical to the previous one, SOCKS5 can also reroute data on the UDP protocol, making it the safest proxy de facto. Furthermore, SOCKS5 protocol allows the proxy owners to enable an internal authentication system as well as the IPv6 support. Then, you can use SOCKS5 proxies with any type of software that uses an Internet connection, such as mail, chat, p2p programs, etc. It is the direct evolution of SOCKS4 protocol.
- Web Proxies (or CGI Proxies) : Web Proxies are actual websites that don’t require any configuration or particular tools on the computer, allowing to directly navigate in anonymity. You can find dozens of these tools online. Here are some we tested for you: whoer.net, hide.me, proxysite.com
How to use Proxies
On the whole Operating System
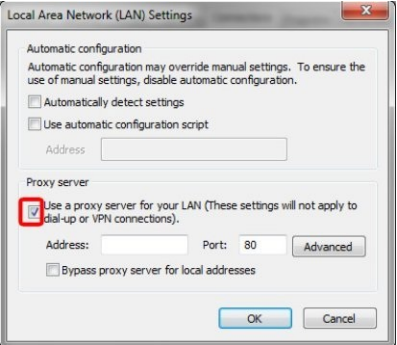
At this point, every user should be able to connect to a proxy, with more or less difficulties, according to the Operating System in use and its version. In example: on Windows you can set a proxy for the entire
computer following this path: Control Panel -> Internet options -> Connections -> LAN settings -> Proxy Server, while you can try different methods at the same time on Windows (but it’s quite confusing). Once you reached the location, you can enter the proxy address and port into the relevant fields.
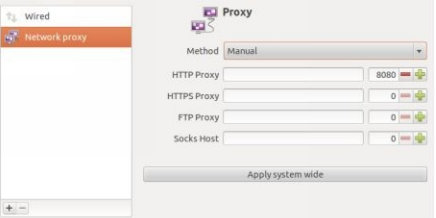
Fortunately, the graphical environments of GNU/Linux make things simpler: on Debian with GNOME 3, you can go to Settings -> Network -Network Proxies.
Proxychains
The proxychains software is one of the best for using proxies in a targeted way; perhaps it is the best proxifier currently available. Unfortunately, its development halted in 2013: the good news is that a fork has been introduced, proxychains-NG. As an advantage, proxychains ensures that any program – and all its dependencies – use only SOCKS4, SOCKS5 or HTTP/S protocols for outbound communications. A word of warning: proxychains is officially available for UNIX systems only, i.e. GNU/Linux, macOS, (via Brew) and BSD. In order to limit any possible issues, we will use the historical version (the deprecated one), still 100% working and available from Debian repositories.
Here’s how to install it:
$ su
$ apt-get install proxychains
$ exit





