A session is the period of time when you as
Penetration testing is also known as pen testing or ethical
Burp Suite is a collection of different tools which are
Cyber Incident Response Planning is always on the radar of
The Cyber Kill Chain offers a comprehensive framework as a
Microsoft Sentinel is a scalable, cloud-native, security information and event
Shadow IT is the use of information technology systems, devices,
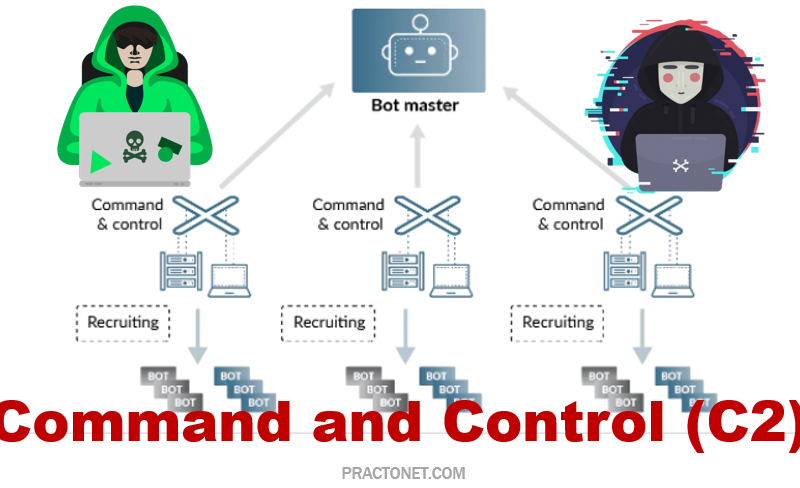
Malicious network attacks have been on the rise in the
The OWASP Top 10 is a standard awareness document for
Zero Trust security is an IT security model that requires