The User-ID feature of the Palo Alto Networks NGFW enables
A single firewall can freely intermix interface types to meet
Penetration testing is also known as pen testing or ethical
Upgrading software is continuous and non ending process for networking
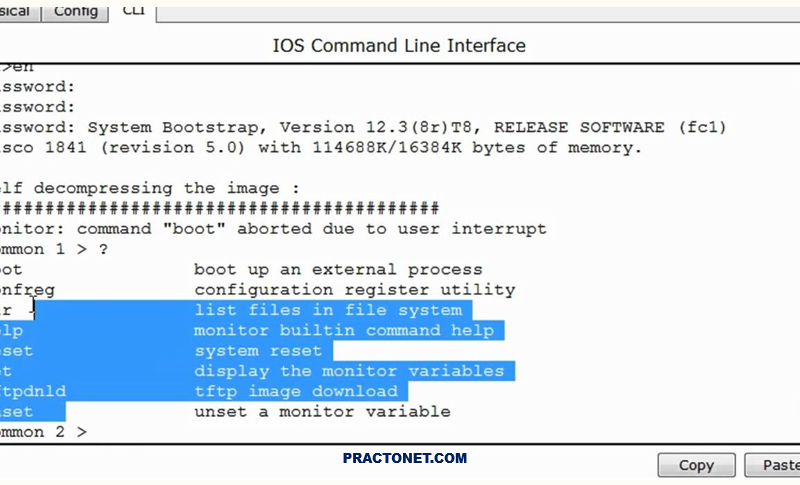
In order to reset a router’s password you must use
Burp Suite is a collection of different tools which are
It is often observed that term information system and information
Cyber Incident Response Planning is always on the radar of
Deploying and maintaining reliable Cisco IOS® software is a priority
Cortex is the industry’s most comprehensive product suite for security