Serverless computing plays an important part in digital transformation. First,
There are numerous differences between serverless computing and other cloud
Serverless computing is a cloud computing execution model that lets
Sandboxing is a cybersecurity practice where you run code, observe
An air gap is a security measure that involves isolating
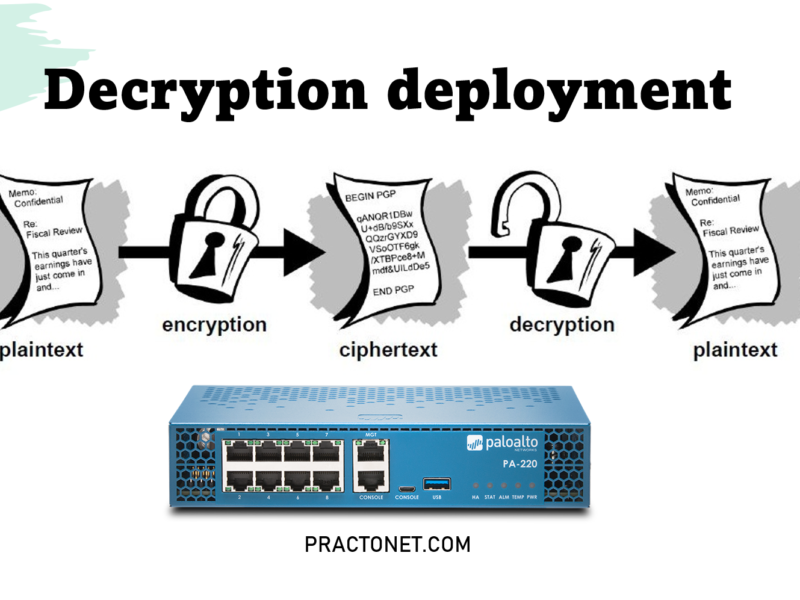
A firewall acting as a decryption broker uses dedicated decryption
The use of encryption for all network applications is growing
There are two main planes that make up a firewall, the data plane and the management plane, which are
We’ve all accidentally sent an email too early, without a
Many people spend considerable amounts of time in their personal