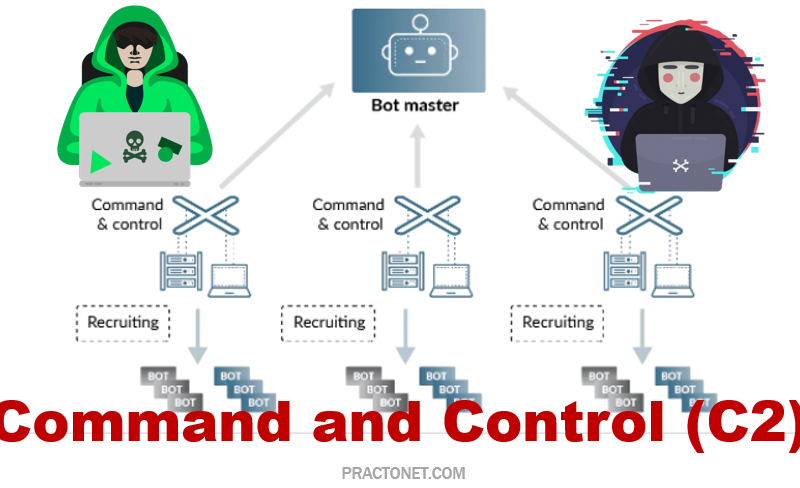
Endpoint device security is most important concern for every for
Malicious network attacks have been on the rise in the
The OWASP Top 10 is a standard awareness document for
Windows Server Update Services (WSUS) and System Center Configuration Manager
SD-WAN is a virtual WAN architecture that provides multi-branch organizations
When it comes to computers, the difference between 32-bit and
Email signatures are common especially in business environments. These signatures
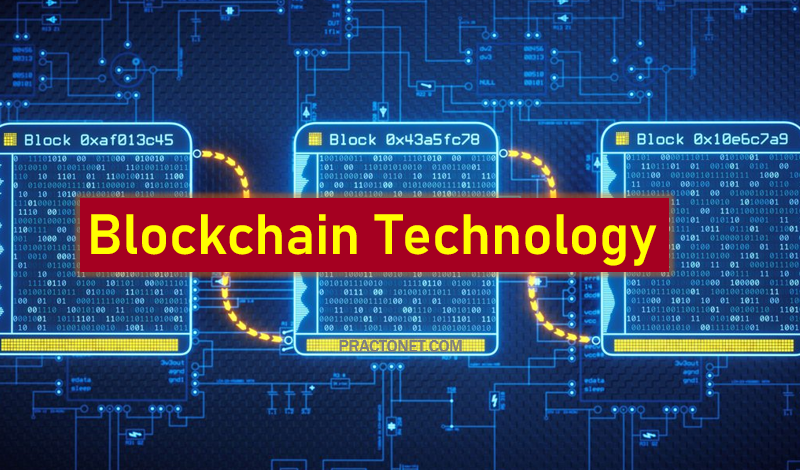
Blockchain is a shared, immutable ledger that facilitates the process
Zero Trust security is an IT security model that requires
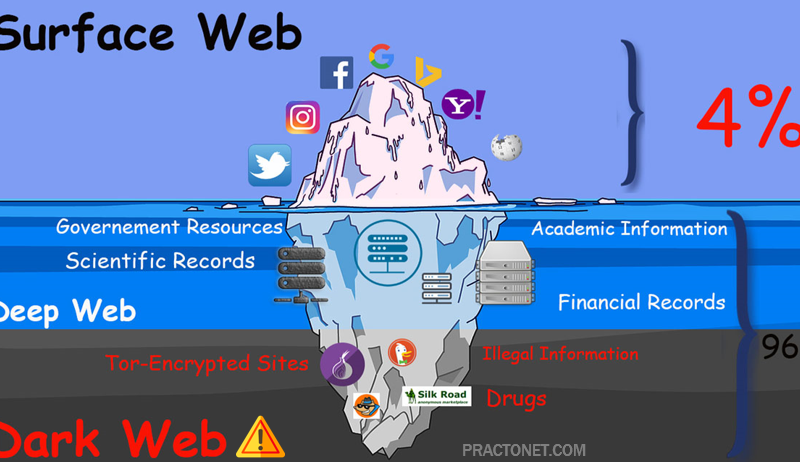
If we imagine web as an ocean, the surface web