A bot is a piece of malware that infects a computer to carry out commands under the remote control of the attacker.
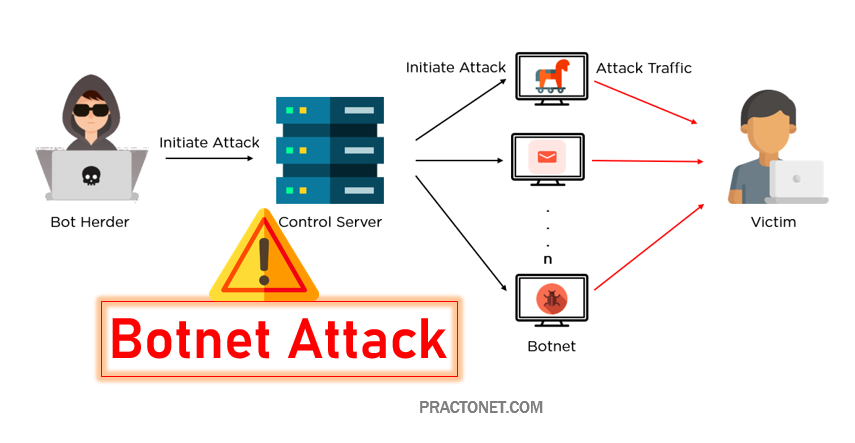
A botnet (short for robot network) is a network of computers infected by malware that are under the control of a single attacking party, known as the bot-herder. Each individual machine under the control of the bot-herder is known as a bot. From one central point, the attacking party can command every computer on its botnet to simultaneously carry out a coordinated criminal action. The scale of a botnet (many comprised of millions of bots) enable the attacker to perform large-scale actions that were previously impossible with malware. Since botnets remain under control of a remote attacker, infected machines can receive updates and change their behavior on the fly. As a result, bot-herders are often able to rent access to segments of their botnet on the black market for significant financial gain.
Common botnet actions include:
Email spam– though email is seen today as an older vector for attack, spam botnets are some of the largest in size. They are primarily used for sending out spam messages, often including malware, in towering numbers from each bot. The Cutwail botnet for example, can send up to 74 billion messages per day. They are also used to spread bots to recruit more computers to the botnet.
DDoS attacks– leverages the massive scale of the botnet to overload a target network or server with requests, rendering it inaccessible to its intended users. DDoS attacks target organizations for personal or political motives or to extort payment in exchange for ceasing the attack.
Financial breach– includes botnets specifically designed for the direct theft of funds from enterprises and credit card information. Financial botnets, like the ZeuS botnet, have been responsible for attacks involving millions of dollars stolen directly from multiple enterprises over very short periods of time.
Targeted intrusions– smaller botnets designed to compromise specific high-value systems of organizations from which attackers can penetrate and intrude further into the network. These intrusions are extremely dangerous to organizations as attackers specifically target their most valuable assets, including financial data, research and development, intellectual property, and customer information.
Why a Botnet?
A botnet is a distributed cyber attack, but there is also a simple DoS—Denial of Service. This type of attack can be sent from a single location, even a single system. The problem with this kind of attack- at least, from the perspective of the attackers – is that it is easy to shut down.
Once it becomes clear that the flood of connection requests is coming from the same place, it can be blocked.
By distributing the requests, so that the flood is coming from thousands – even tens of thousands – the attackers make it essentially impossible to block the source. Further compounding their problems is the fact that the sources are mostly innocent users who might not even know their system has been compromised, which raises questions about merely blocking them.
Protecting Your System From Becoming Part of a Botnet
If you have a computer, server, or even a smartphone or tablet, you could unwittingly become part of a botnet. Fortunately, it’s easy to stay safe, and much of what you need to do is what should be considered standard online safety.
Keeping your device’s operating systems up to date, exercising common sense about where you go online and what you click on, and using a decent anti-virus software to keep malicious software clean should be enough for the vast majority of users.