The OSI transport layer (Layer 4) defines several functions, the most important of which are error recovery and flow control. Likewise, the TCP/IP transport layer protocols also implement these same types of features. Note that both the OSI model and the TCP/IP model call this layer the transport layer. But as usual, when referring to the TCP/IP model, the layer name and number are based on OSI, so any TCP/IP transport layer protocols are considered Layer 4 protocols.
The key difference between TCP and UDP is that TCP provides a wide variety of services to applications, whereas UDP does not. For example, routers discard packets for many reasons, including bit errors, congestion, and instances in which no correct routes are known. As you have read already, most data-link protocols notice errors (a process called error detection) but then discard frames that have errors. TCP provides retransmission (error recovery ) and helps to avoid congestion (flow control), whereas UDP does not. As a result, many application protocols choose to use TCP.
Each TCP/IP application typically chooses to use either TCP or UDP based on the application’s requirements. For example, TCP provides error recovery, but to do so, it consumes more bandwidth and uses more processing cycles. UDP does not perform error recovery, but it takes less bandwidth and uses fewer processing cycles. Regardless of which of these two TCP/IP transport layer protocols the application chooses to use, you should understand the basics of how each of these transport layer protocols works.
TCP relies on IP for end-to-end delivery of the data, including routing issues. In other words, TCP performs only part of the functions necessary to deliver the data between applications. Also, the role that it plays is directed toward providing services for the applications that sit at the endpoint computers. Regardless of whether two computers are on the same Ethernet, or are separated by the entire Internet, TCP performs its functions the same way. Let’s know about OSI reference and TCP/IP model:
OSI Reference Model
A network reference model serves as a blueprint, dictating how network communication should occur. The OSI model was the first true network model , and consisted of seven layers. The Open Systems Interconnection (OSI) model was developed in the 1970’s and formalized in 1983 by the International Organization for Standardization (ISO). The OSI Model consists of seven layers, each corresponding to a particular network function:
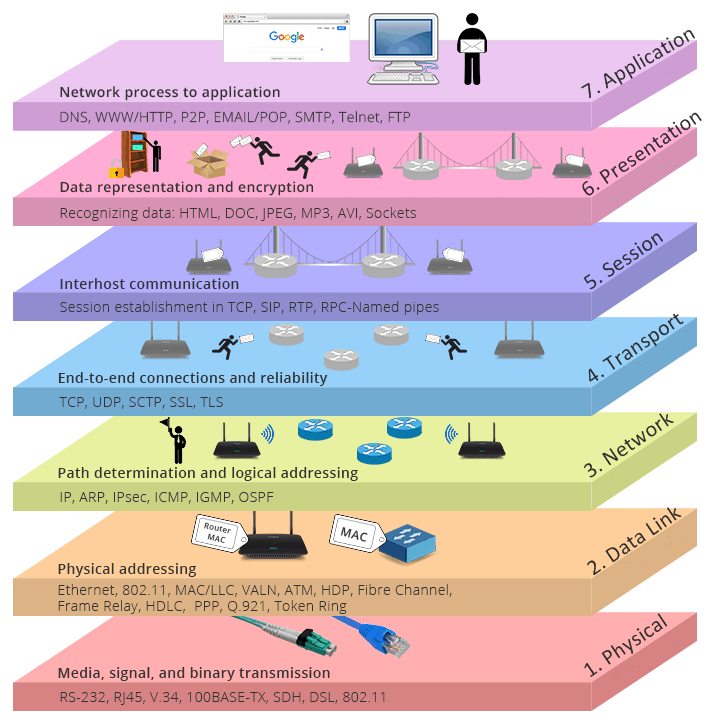
Layer 7 Application Layer
Application layer consists of protocols that focus on process-to-process communication across an IP network and provides a firm communication interface and end-user services.It is also called User layer because it provides interaction to User. Example: SMTP, DHCP, FTP, HTTP, HTTPS etc PDU format is DATA.
Layer 6 Presentation Layer
Presentation layer is used to present data to the application layer in an accurate, well-defined and standardized format. It provides proper format to the file. Encryption & Decryption and Compression & Decompression is done. Example : Text, Images, Videos, Audio etc. PDU format is DATA.
Layer 5 Session Layer
Session layer is the fifth layer and provides the mechanism for opening, closing and managing a session between end-user application processes. It creates different session for different session ID with the help of Port number. Port no. is of 16 bit (0-65535) value. Port are of 2 types. Well known ports(0-1023) & Open ports (1024-65535). Example: FTP-80, DNS-53, DHCP-67/68. PDU format is DATA.
Layer 4 Transport Layer
The transport layer is the fourth layer in the open system interconnection model responsible for end-to-end communication over a network. Transport layer ensures the reliable arrival of messages and provides error checking mechanisms and data flow controls. It provides transparent transfer of data between end systems using the services of the network. There are 2 Services in Transport layer i.e TCP and UDP
- TCP stands for Transmission Control Protocol, It is Connection Oriented, Slow but Reliable transport protocol.
- UDP stands for User Datagram Protocol, It is Connection Less, fast but Unreliable transport protocol.
PDU format is SEGMENT.
Layer 3 Network Layer
The network layer is the third level of the Open Systems Interconnection ModelOSI Model and the layer that provides data routing paths for network communication. Data is transferred in the form of packets via logical network paths in an ordered format controlled by the network layer. L3 is responsible for Best path selection between Source to Destination. Example: EIGRP, OSPF, VRRP, PIM, ICMP etc PDU format is PACKET.
Layer 2 Data Link Layer
The data link layer is the second layer of the OSI model & It is most reliable node to node delivery of data. It forms frames from the packets that are received from network layer and gives it to physical layer. Data-link layer is responsible for implementation of point-to-point flow and error control mechanism. Flow Control. Example, CDP, ARP, PPP, FDDI etc It has a 2 sub layer: LLC sublayer & MAC sublayer.
- LLC-Logical Link Control is the upper sublayer of L2 and it performs Error control, Framing, Flow control & responsible for identifying different protocol logicaly.
- MAC is the lower sublayer of L2 and it frames data received from the upper layer and passes them to the physical layer. It also defines how to transmit data on physical layer. Example CSMA/CD.
PDU format is FRAME.
Layer 1 Physical Layer
The physical layer is the lower layer of the OSI Model and it deals with bit-level transmission between different devices. Example: Cables, NIC, Hub, Repeater etc. PDU format is BITS.
TCP/IP Model
TCP/IP also is a layered protocol but does not use all of the OSI layers. OSI model was theoretical model and protocol-independent standard but TCP/IP is the model aroung which Network or internet is developed and it is protocol-dependent model.It is occasionally known as the Department of Defense (DoD) model, because the development of the networking model was funded by DARPA. The TCP/IP Model consists of four layers:
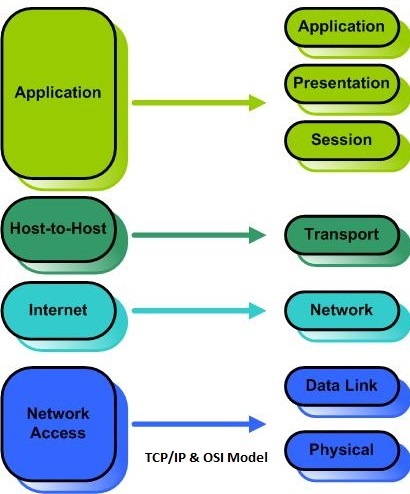
Layer 4 Application Layer
The Application layer provides applications the ability to access the services of the other layers and defines the protocols that applications use to exchange data. IN TCP/IP Application layer is the Combined layer of Application, Presentation & Session Layer of the OSi model. Application layer in TCP/IP also performs Encryption, Decryption along with helps on creating Sessions. Example of Application Layer Protocol are BGP, DHCP, DNS, TELNET, HTTP etc.
Layer 3 Host-to-Host (Transport) Layer
Host to Host layer is equivalent to Network Layer of OSI model. It provides the services for Secure data transmission from Source and Destination. ensures the reliable arrival of messages and provides error checking mechanisms and data flow controls. It provides transparent transfer of data between end systems using the services of the network. It uses 2 Services i.e TCP and UDP.
Layer 2 Internet layer
The Internet layer is responsible for addressing, packaging, and routing functions. This layer is equivalent to Network Layer of OSI Model. Internet Layer is responsible to provide best path to reach destination. The core protocols of the Internet layer are IP, ARP, ICMP, and IGMP.
Layer 1 Network Access Layer
Network Access layer is responsible for placing TCP/IP packets on the network medium and receiving TCP/IP packets off the network medium. TCP/IP was designed to be independent of the network access method, frame format, and medium. In this way, TCP/IP can be used to connect differing network types. These include LAN technologies such as Ethernet and Token Ring and WAN technologies such as Frame Relay. Network Access layer encompasses the Data Link and Physical layers of the OSI model.
TCP Connection Establishment and Termination (3 Way handshake)
TCP connection establishment occurs before any of the other TCP features can begin their work. Connection establishment refers to the process of initializing Sequence and Acknowledgment fields and agreeing on the port numbers used.
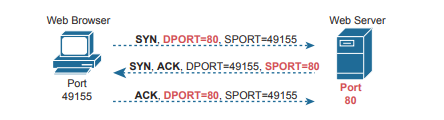
This three-way connection establishment flow (also called a three-way handshake) must complete before data transfer can begin. The connection exists between the two sockets, although the TCP header has no single socket field. Of the three parts of a socket, the IP addresses are implied based on the source and destination IP addresses in the IP header. TCP is implied because a TCP header is in use, as specified by the protocol field value in the IP header. Therefore, the only parts of the socket that need to be encoded in the TCP header are the port numbers.
TCP signals connection establishment using 2 bits inside the flag fields of the TCP header. Called th e SYN and ACK flags, these bits have a particularly interesting meaning. SYN means “synchronize the sequence numbers,” which is one necessary component in initialization for TCP.
This four-way termination sequence is straightforward and uses an additional flag, called the FIN bit. (FIN is short for “finished,” as you might guess.) One interesting note: Before the device on the right sends the third TCP segment in the sequence, it notifies the application that the connection is coming down. It then waits on an acknowledgment from the application before sending the third segment in the figure. Just in case the application takes some time to reply, the PC on the right sends the second flow in the figure, acknowledging that the other PC wants to take down the connection. Otherwise, the PC on the left might resend the first segment repeatedly.
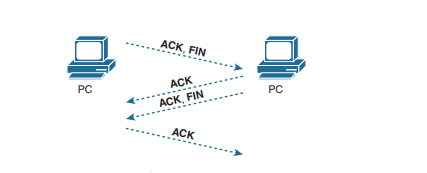
TCP establishes and terminates connections between the endpoints, whereas UDP does not. Many protocols operate under these same concepts, so the terms connection-oriented and connectionless are used to refer to the general idea of each. More formally, these terms can be defined as follows:
- Connection-oriented protocol: A protocol that requires an exchange of messages before data transfer begins, or that has a required pre-established correlation between two endpoints.
- Connectionless protocol: A protocol that does not require an exchange of messages and that does not require a pre-established correlation between two endpoints.
Compare TCP and UDP Protocol
TCP/IP helps you to determine how a specific computer should be connected to the internet and how you can transmit data between them. It helps you to create a virtual network when multiple computer networks are connected. TCP/IP stands for Transmission Control Protocol/ Internet Protocol. It is specifically designed as a model to offer highly reliable and end-to-end byte stream over an unreliable internetwork.
UDP is a Datagram oriented protocol. It is used for broadcast and multicast type of network transmission. The full form of UDP is User Datagram Protocol (A datagram is a transfer unit associated with a packet-switched network.) The UDP protocol works almost similar to TCP, but it throws all the error-checking stuff out, all the back-and-forth communication and deliverability.
| TCP | UDP |
|---|---|
| It is a connection-oriented protocol. | It is a connectionless protocol. |
| TCP reads data as streams of bytes, and the message is transmitted to segment boundaries. | UDP messages contain packets that were sent one by one. It also checks for integrity at the arrival time. |
| TCP messages make their way across the internet from one computer to another. | It is not connection-based, so one program can send lots of packets to another. |
| TCP rearranges data packets in the specific order. | UDP protocol has no fixed order because all packets are independent of each other. |
| The speed for TCP is slower. | UDP is faster as error recovery is not attempted. |
| Header size is 20 bytes. | Header size is 8 bytes. |
| TCP is heavy-weight. TCP needs three packets to set up a socket connection before any user data can be sent. | UDP is lightweight. There are no tracking connections, ordering of messages, etc. |
| TCP does error checking and also makes error recovery. | UDP performs error checking, but it discards erroneous packets. |
| Acknowledgment segments. | No Acknowledgment segments. |
| Using handshake protocol like SYN, SYN-ACK, ACK. | No handshake (so connectionless protocol). |
| TCP is reliable as it guarantees delivery of data to the destination router. | The delivery of data to the destination can’t be guaranteed in UDP. |
| TCP offers extensive error checking mechanisms because it provides flow control and acknowledgment of data. | UDP has just a single error checking mechanism which is used for checksums. |
Application of TCP
- It helps you to establish/set up a connection between different types of computers.
- Operates independently of the operating system.
- Supports many routing-protocols.
- It enables the internetworking between the organizations.
- It can be operated independently.
- Supports several routing protocols.
- TCP can be used to establish a connection between two computers.
Application of UDP
- UDP method is largely used by time-sensitive applications as well as by servers that answer small queries from a larger client base.
- UDP is compatible with packet broadcasts for sending all over the network and for multicasting sending.
- It is also used in Domain Name System, Voice over IP, and online games.
When to use UDP and TCP?
- TCP is an ideal choice, and even it has associated overhead, Therefore, when most of the overhead is in the connection, your application stays connected for any length of time.
- UDP is ideal to use with multimedia like VoIP.
- Use TCP sockets when both client and server independently send packets at that time; an occasional delay is acceptable.
- You should use user UDP if both client and server may separately send packets, and occasional delay is also not acceptable.
HTTP
HTTP is an abbreviation of Hyper Text Transfer Protocol and is an application protocol to enable communication between physically dispersed systems. It was originally devised by Sir Tim Berners Lee in 1989. It is now coordinated by the W3C. In its most basic format it forms the basis for how web pages are communicated from the web server to the user’s browser. Hyper Text itself is the text used on web pages which connects one page to another page, whether within the same system or externally. It is the links that connect content on the internet.
How Does HTTP Work?
HTTP is an Application Protocol for transferring Resources across the internet. HTTP uses Port 80. Which is the port that the Web Server accepts requests from. Most Resources are files (images, etc.) but can include other data such as output from scripts. HTTP sessions are opened by an HTTP Client (i.e. the user’s browser) via a user agent and a connection Request Message is sent to an HTTP Server (i.e. the Web Server). The Request Message is also known as the ‘Client Request’ and consists of the following lines:
Request line
Headers
An empty line
An optional message body
Once the response has been delivered the Web Server closes the connection. This type of connection is known as Stateless in that it exists only for the duration of the data exchange. Depending on the availability or otherwise of the Resource HTTP provides an appropriate status code (also referred to as the ‘Server Response’) determined by the protocol. These are as follows:
1xx – an informational message only
2xx – success of some kind, e.g: 200 OK – file found
3xx – the client to another URL, e.g: 301 moved permanently
4xx – an error on the client’s part, e.g: 404 – file not found
5xx – an error on the server’s part, e.g: 500 server error





