A simple password string is the single factor that a user must enter to be authenticated. Because a password should be remembered and not written down anywhere, you might think of your password as “something you know.” Hopefully nobody else knows it too; otherwise, they could use it to impersonate you when authenticating.
An enterprise might also consider using alternative credentials that bring more complexity and more security. Multifactor credentials require users to provide values or factors that come from different sources, reducing the chance that an attacker might possess all of the factors. An old saying describes two-factor credentials as “something you have” (a dynamic changing cryptographic key or a text message containing a time-limited code) and “something you know” (a password).
A digital certificate can serve as one alternative factor because it serves as a trusted form of identification, adheres to a standardized format, and contains encrypted information. If an enterprise supports certificate use, then a user must request and be granted a unique certificate to use for specific purposes. For example, certificates used for authenticating users must be approved for authentication. In order to be trusted, certificates must be granted and digitally signed by a trusted certificate authority (CA). As long as the services used by the enterprise know and trust the CA, then individual certificates signed by that CA can be trusted as well.
Digital certificates are also time sensitive, as each is approved for a specific time range. Once a certificate expires, any attempts to authenticate with it will be rejected. The user who possesses the certificate can request a new one prior to the expiration date or at any time afterward. Certificates can also be revoked, if the business decides to revoke privileges from a user, if the user separates from the business, and so on. Even if the user still possesses a revoked certificate, he will be refused access when he tries to authenticate with it.
Because digital certificates exist as files on a computer or device, you might think they can be freely copied and used to identify people other than the original owners. Each digital certificate must also carry proof of possession to show that it was truly granted to the user who presents it during authentication. This proof is built into the encrypted certificate content, as a result of combining public keys that the user’s machine and the authentication server can publicly share, along with private keys that each party keeps private and secret. As long as the authentication server can verify that the certificate was created using the correct public and private keys, then the certificate must be possessed by the expected owner. If not, then authentication will be rejected to keep an imposter out.
Biometric credentials carry the scheme even further by providing a factor that represents “something you are.” The idea is to use some physical attribute from a user’s body to uniquely identify that person. Physical attributes are usually unique to each individual’s body structure and cannot be easily stolen or duplicated. For example, a user’s fingerprint can be scanned and used as an authentication factor. Other examples include face recognition, palm prints, voice recognition, iris recognition, and retinal scans. As you might expect, some methods can be trusted more than others. Sometimes facial recognition systems can be fooled when presented with photographs or masks of trusted individuals. Injuries and the aging process can also alter biometric patterns such as fingerprints, facial shapes, and iris patterns. To help mitigate potential weaknesses, multiple biometric credentials can be collected and used to authenticate users as well.
Let’s discuss more about Digital certificate, Multifactor and Biometric authentication.
Certificate-Based Authentication
Certificate-based authentication is the use of a Digital Certificate to identify a user, machine, or device before granting access to a resource, network, application, etc. In the case of user authentication, it is often deployed in coordination with traditional methods such as username and password. One differentiator of certificate-based authentication is that unlike some solutions that only work for users, such as biometrics and one time passwords (OTP), the same solution can be used for all endpoints – users, machine, devices and even the growing Internet of Things (IoT).
Why Is Certificate-Based Authentication Used?
Ease of deployment and ongoing management: Most certificate-based solutions today come with a cloud-based management platform that makes it easy for administrators to issue certificates to new employees, renew certificates and revoke certificates when an employee leaves the organization. Solutions that integrate with Active Directory can make the enrollment and issuance process even easier, by enabling auto enrollment and silent installations. Unlike some authentication methods like biometrics or OTP tokens, there is no additional hardware needed. Certificates are stored locally on the machine or device. This not only saves on costs, but can also alleviate management pains around distributing, replacing and revoking tokens.
User-friendly: There’s always a tradeoff between increasing security and the costs involved and burden on end users. Most people don’t think of it, but using certificates is very easy for end users. After the certificate is installed (and in some cases, this can happen automatically), there is nothing further to be done. Additionally, most enterprise solutions already support certificate-based authentication.
Leverage existing access control policies: You can also easily leverage existing group policies and permissions to control which users and machines can access different applications and networks. This way you can ensure only privileged users can access sensitive or critical operations.
Mutual authentication: Another benefit of using certificates is that it allows for mutual authentication, meaning both parties involved in a communication are identifying themselves, whether that communication is from a user-to-user or a user-to-machine or machine-to-machine. For example, a client must prove its identity to a company intranet and the intranet must prove its identity to the client, before a connection can be made.
Extending to external users: Certificates are also easy to roll out to users outside of your organization (e.g. partners, independent contractors and freelancers) who may need to access your networks. They won’t need additional software on their local machine and the ease-of use means you won’t need to provide much additional training.
How is Certificate-Based Authentication Used?
Certificate-based authentication is quite flexible and can be used in a number of ways, but here are some of the most common use cases we hear from our customers. You’ll notice the common theme with all of these and certificate-based authentication in general, is to allow access only to approved users and machines and prevent unauthorized users or rogue machines.
- User authentication
- Windows Logon
- Accessing corporate email, internal networks, or intranets
- Accessing cloud-based services, such as Google Apps, SharePoint and Salesforce
- Machine and device authentication
- Identifying on-location/in-field machines that need to communicate with back-end services (e.g. payment kiosks located in convenience stores)
- Identifying all employee laptops and mobile devices before allowing access to WiFi networks, VPNs, Gateways, etc.
- Identifying all servers within the enterprise to enable mutual authentication
Multi-factor authentication (MFA)
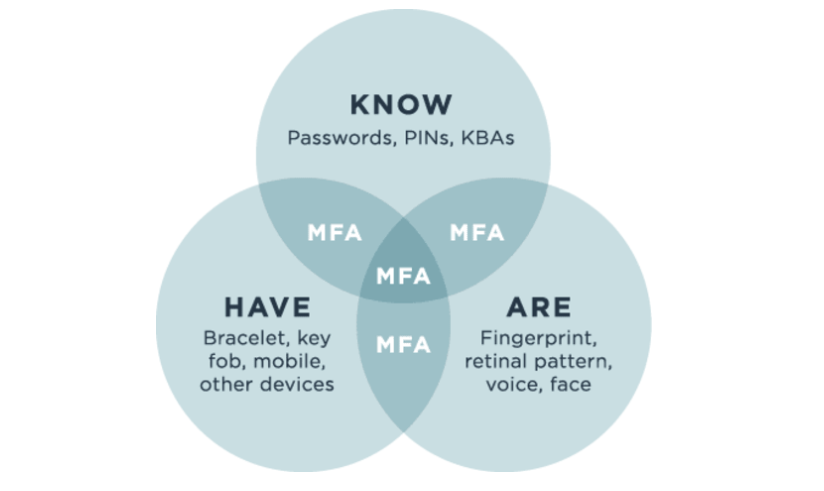
Multi-factor authentication (MFA) is used to ensure that digital users are who they say they are by requiring that they provide at least two pieces of evidence to prove their identity. Each piece of evidence must come from a different category: something they know, something they have or something they are.
If one of the factors has been compromised by a hacker or unauthorized user, the chances of another factor also being compromised are low, so requiring multiple authentication factors provides a higher level of assurance about the user’s identity.
What are the benefits of multi-factor authentication?
Passwords may reign supreme as the most common way to authenticate your online identity, but they increasingly provide very little protection. Once a password is stolen, hackers can use those credentials to log in to applications and business systems, bypass other access controls and wreak serious havoc. In fact, according to the 2020 Verizon Data Breach Investigations Report, stolen login credentials are the top tactic used by hackers to achieve data breaches.
And there are an alarming variety of attack vectors hackers can take advantage of to steal passwords or gain access, including phishing attacks, brute force attacks, web app attacks, point of sale intrusions and even stolen hardware.
Multi-factor authentication provides a layer of protection for both employees and customers that addresses all of these weaknesses. It mitigates the ripple effect of compromised credentials—a bad actor may steal your username and password, but if they’re prompted for another factor before they can access critical data, make a transaction or log into your laptop, they’ll be sunk.
How does multi-factor authentication work?
A user’s credentials must come from at least two of three different categories, or factors. Two-factor authentication, or 2FA, is a subset of MFA where only two credentials are required, but MFA can use any number of factors.
Some organizations may want to set up multi-factor authentication for all users, employees and customers alike. It’s especially effective when combined with a single sign-on (SSO) solution, which removes many passwords from the equation, strengthening security even further and improving the user experience.
That said, some organizations may not feel the need to require MFA in all cases. To optimize employee and customer convenience, they might choose to bypass MFA in low-risk scenarios, while requiring stronger security in high-risk situations, for particularly sensitive data or for high-value transactions. For example:
- A bank may allow a customer to log into his online account with just a username and password, but require a second authentication factor before transactions can be approved.
- An organization may want a higher level of assurance that an employee is who she claims to be when accessing an HR application from a coffee shop or other off-domain location.
- A retailer may set up MFA to kick in when a vendor logs into their portal from a new device, to make sure it’s not a hacker trying to get in with a stolen password.
This kind of multi-factor authentication is called contextual, adaptive or risk-based MFA. The beauty of using contextual MFA is that it can strengthen security only when warranted, and these requirements or use cases can easily change and evolve over time.
Biometric Security
It involves using biometric security software to automatically recognise people based on their behavioural or biological characteristics. The biometric technology currently used most often in physical access control is fingerprint recognition because of its lower price. Among 2D fingerprint sensors, multispectral sensors are often a better choice over optical sensors. They’re slightly more expensive but offer higher accuracy and more reliable performance.
Other identifiers used include finger veins, palm veins, faces and irises. For high-security environments, iris recognition provides the best accuracy, followed by palm vein recognition. Some biometric security systems verify identities using one or more detection technologies, while others don’t verify the identity at all to keep costs low.
What benefits do biometric security systems offer?
Strengthen security: One of the key benefits of biometric security devices is that they can help to increase your protection. It’s much harder, for example, to clone or steal a fingerprint than an access card. In situations where you need to increase security, biometrics can also be used for multifactor verification. After someone’s presented their badge, for example, they then need to present their fingerprint to verify that they are who they claim to be. This is safer than using a PIN for verification as that can easily be passed to other people.
Improve convenience: Biometric security systems can also offer users more convenience. It’s easy to forget a card or key, but you always have your biometrics with you. And if the identifier allows handsfree or long-distance recognition, the convenience levels increase further – you may be allowed to enter your building simply by having your face scanned as you pass the entrance.





