Security in cloud computing is a major concern. Data in cloud should be stored in encrypted form. To restrict client from accessing the shared data directly, proxy and brokerage services should be employed.
Security Planning
Before deploying a particular resource to cloud, one should need to analyze several aspects of the resource such as:
- Select resource that needs to move to the cloud and analyze its sensitivity to risk.
- Consider cloud service models such as IaaS, PaaS, and SaaS. These models require customer to be responsible for security at different levels of service.
- Consider the cloud type to be used such as public, private, community or hybrid.
- Understand the cloud service provider’s system about data storage and its transfer into and out of the cloud.
Knowing Security of Cloud
A particular service model defines the boundary between the responsibilities of service provider and customer. Cloud Security Alliance (CSA) stack model defines the boundaries between each service model and shows how different functional units relate to each other.
Key Points to CSA Model
- IaaS is the most basic level of service with PaaS and SaaS next two above levels of services.
- Moving upwards, each of the service inherits capabilities and security concerns of the model beneath.
- IaaS provides the infrastructure, PaaS provides platform development environment, and SaaS provides operating environment.
- IaaS has the least level of integrated functionalities and integrated security while SaaS has the most.
- This model describes the security boundaries at which cloud service provider’s responsibilities end and the customer’s responsibilities begin.
- Any security mechanism below the security boundary must be built into the system and should be maintained by the customer.
Knowing Data Security
Since all the data is transferred using Internet, data security is of major concern in the cloud. Here are key mechanisms fo0r protecting data.
- Access Control
- Auditing
- Authentication
- Authorization
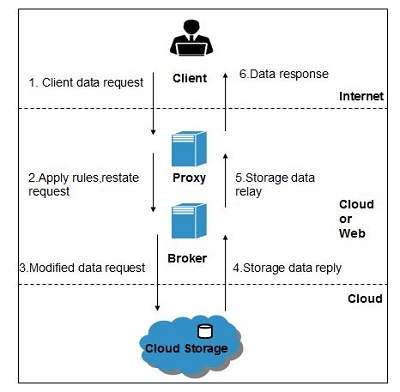
Since data stored in cloud can be accessed from anywhere, we must have a mechanism to isolate data and protect it from client’s direct access. Brokered Cloud Storage Access is an approach for isolating storage in the cloud. In this approach, two services are related:
- A broker with full access to storage but no access to client.
- A proxy with no access to storage but access to both client and broker.
Working Of Brokered Cloud Storage Access System
When the client issues request to access data:
- The client data request goes to the external service interface of proxy.
- The proxy forwards the request to the broker.
- The broker requests the data from cloud storage system.
- The cloud storage system returns the data to the broker.
- The broker returns the data to proxy.
- Finally the proxy sends the data to the client.
Encryption helps to protect data from being compromised. It protects data that is being transferred as well as data stored in the cloud. Although encryption helps to protect data from any unauthorized access, it does not prevent data loss.
Cloud Computing Application
Cloud Computing has its applications in almost all the fields such as business, entertainment, data storage, social networking, management, entertainment, education, art and global positioning system, etc.
Cloud computing has made businesses more collaborative and easy by incorporating various apps such as MailChimp, Chatter, Google Apps for business, and QuickBooks.
Data Storage and Backup
Box.com, Mozy, Joukuu are the applications offering data storage and backup services in cloud.
Management Applications
There are apps available for management task such as time tracking, organizing notes. Applications performing such tasks are Toggl, Evernote, Outright.
Data Storage and Backup
Box.com, Mozy, Joukuu are the applications offering data storage and backup services in cloud.
More application are Social application like Facebook, Twitter and Entertainment Applications, Art Applications and more.