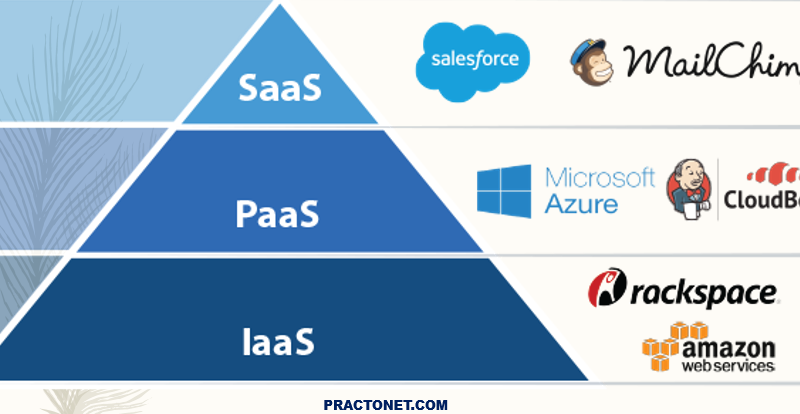
Cloud models come in three types: SaaS (Software as a
There are four cloud deployment models: public, private, community, and
Cloud Computing architecture comprises of many cloud components, which are
There are certain technologies working behind the cloud computing platforms
Cloud Computing refers to manipulating, configuring, and accessing the hardware
The premier text editor for Linux and UNIX is a
Adding content to files in Linux can be done in
The passwd command is used to update a user’s password.
Package management is a system by which software can be
Running a command results in something called a process. In